
Author: Jonelle E. Morris
Title: Management Information System
Area:
Country: United States
Program:
Available for Download: Yes
View More Student Publications Click here
Sharing knowledge is a vital component in the growth and advancement of our society in a sustainable and responsible way. Through Open Access, AIU and other leading institutions through out the world are tearing down the barriers to access and use research literature. Our organization is interested in the dissemination of advances in scientific research fundamental to the proper operation of a modern society, in terms of community awareness, empowerment, health and wellness, sustainable development, economic advancement, and optimal functioning of health, education and other vital services. AIU’s mission and vision is consistent with the vision expressed in the Budapest Open Access Initiative and Berlin Declaration on Open Access to Knowledge in the Sciences and Humanities. Do you have something you would like to share, or just a question or comment for the author? If so we would be happy to hear from you, please use the contact form below.
For more information on the AIU's Open Access Initiative, click here.
Introduction
Management Information System a challenging and constantly changing field of study It involves the innovative application of computer technology and analytical skills to know and understand the needs of customers, effectively manage operations and supply chain issues, create new efficiencies and competitive advantages and realize the growing promise of e-commerce
Management information systems increasingly change people’s lives, including relationships, communications, transactions, data collection and decision-making. Changes in IT lead to innovation, new business models and services. Organizational leaders need to consider the impact of change inside their organizations. Business must constantly examine its performance, strategy, processes and systems in order to monitor the changes to be made.
The concept of change management and how people deal with it has gained much attention in the fields of human and organizational behaviour, psychology, business administration, operation management, and information systems. Technology and business improvements are needed in modern society, and finding effective ways for managing the process of changes is the key to success in a highly competitive and global business environment
Management Information System (MIS) enables easy access to corporate data such as student, staff, research and finance. The software allows for accessing data via a click and point structure allowing users to drill down to the level of detail that interests them. What data is displayed can be limited by the user by selecting various slices of the data to provide subsets that meet their particular needs. It supports the decision making processes and helps ensure that resource allocation and planning are founded on accurate and meaningful information which at present is drawn entirely from the central University databases. Management Information System vital organizational resources and constitute an integral part of managerial decision making. Therefore, it is important to understand how IS can be better used to assist managers and organizations to improve efficiency, differentiate markets and services, enhance performance and improve productivity while protecting organizational assets.
We are in the world of advanced Information Technology where things are moving in such a fast phase. The availability of information becomes cheaper and faster and the facilities existing to exchange the information among users all across the world has become more simpler due to the evolving of Information Super Highway. The internet provides fast and inexpensive communication channels that range from messages posted on bulletin boards to complex exchanges among many organisations. It also includes information transfer (among computers) and information processing. E-mail, chat groups, and newsgroups are examples of major communication media.
General Analysis
The development and management of information technology tools assists executives and the general workforce in performing any tasks related to the processing of information. MIS systems are especially useful in the collation of business data and the production of reports to be used as tools for decision making.
With computers being as ubiquitous as they are today, there's hardly any large business that does not rely extensively on their IT systems.
However, there are several specific fields in which MIS has become invaluable.
* Strategy Support
While computers cannot create business strategies by themselves they can assist management in understanding the effects of their strategies, and help enable effective decision-making.
MIS systems can be used to transform data into information useful for decision making. Computers can provide financial statements and performance reports to assist in the planning, monitoring and implementation of strategy.
MIS systems provide a valuable function in that they can collate into coherent reports unmanageable volumes of data that would otherwise be broadly useless to decision makers. By studying these reports decision-makers can identify patterns and trends that would have remained unseen if the raw data were consulted manually.
MIS systems can also use these raw data to run simulations – hypothetical scenarios that answer a range of ‘what if’ questions regarding alterations in strategy. For instance, MIS systems can provide predictions about the effect on sales that an alteration in price would have on a product. These Decision Support Systems (DSS) enable more informed decision making within an enterprise than would be possible without MIS systems.
* Data Processing
Not only do MIS systems allow for the collation of vast amounts of business data, but they also provide a valuable time saving benefit to the workforce. Where in the past business information had to be manually processed for filing and analysis it can now be entered quickly and easily onto a computer by a data processor, allowing for faster decision making and quicker reflexes for the enterprise as a whole.
Management by Objectives
While MIS systems are extremely useful in generating statistical reports and data analysis they can also be of use as a Management by Objectives (MBO) tool.
MBO is a management process by which managers and subordinates agree upon a series of objectives for the subordinate to attempt to achieve within a set time frame. Objectives are set using the SMART ratio: that is, objectives should be Specific, Measurable, Agreed, Realistic and Time-Specific.
The aim of these objectives is to provide a set of key performance indicators by which an enterprise can judge the performance of an employee or project. The success of any MBO objective depends upon the continuous tracking of progress.
In tracking this performance it can be extremely useful to make use of an MIS system. Since all SMART objectives are by definition measurable they can be tracked through the generation of management reports to be analysed by decision-makers.
Benefits of MIS
The field of MIS can deliver a great many benefits to enterprises in every industry. Expert organisations such as the Institute of MIS along with peer reviewed journals such as MIS Quarterly continue to find and report new ways to use MIS to achieve business objectives.
Core Competencies
Every market leading enterprise will have at least one core competency – that is, a function they perform better than their competition. By building an exceptional management information system into the enterprise it is possible to push out ahead of the competition. MIS systems provide the tools necessary to gain a better understanding of the market as well as a better understanding of the enterprise itself.
Enhance Supply Chain Management
Improved reporting of business processes leads inevitably to a more streamlined production process. With better information on the production process comes the ability to improve the management of the supply chain, including everything from the sourcing of materials to the manufacturing and distribution of the finished product.
Quick Reflexes
As a corollary to improved supply chain management comes an improved ability to react to changes in the market. Better MIS systems enable an enterprise to react more quickly to their environment, enabling them to push out ahead of the competition and produce a better service and a larger piece of the pie.
Business Data Communication and Networks
Introduction
In recent years, the world of communications has undergone enormous changes. In fact, the term paradigm shift has become ordinary in the information systems field. However, it is definitely an appropriate descriptor of the communications industry. The primary focus of computer technology in the past was to provide processing power for increasingly hungry but traditional applications, such as word processing, spreadsheet, and database applications. While computing power for application processing is still important, today's computer buyers are paying at least as much if not more attention to the computer's ability to connect to networks. In fact, some computer systems (for example, network PCs and Web TVs) have been developed primarily to connect to networks. These computers rely on other computer systems connected to a network to do most of the processing. This change in emphasis is affecting how computer systems impact individuals, organizations, and society by placing more information, even more computing power, at everyone's fingertips.
Transmission of voice, data, text, sound, and images pervades computer information systems regardless of the size of a manager's computer resources. Consider the diversity of organizational tasks that now depend on some form of communications system, The laws governing communications also have been changing rapidly, opening up opportunities for competition between industry giants who had enjoyed monopolies in their areas or were at least restricted from entering other communications areas. The most recent change is the Telecommunications Act of 1996. The basic purpose of this act is to permit any business to compete in any communications market. The law blurs traditional demarcations in industry "turf." For example, cable TV companies used to be confined to offering TV entertainment. These same companies are now considering offering voice communications over their cable system and have already begun to enter the arena of data communications by providing Internet access to their subscribers. At the same time, more and more video and voice conversations are being transmitted over the Internet, and telephone companies have been given the right to provide cable service to their customers. Entertainment firms have begun to purchase or make alliances with telephone, cable, and satellite broadcasting companies. Major TV networks have created alliances with major software firms, and local telephone companies have entered the long-distance telephone market. Some PHS stations have begun to embed data in their TV broadcasts, allowing PCs with a special card installed to receive the data. Even power companies are considering entering the communications business because of the important rights of way to our homes and businesses that they already possess
After seeing the basics and the components of a network, now we are going to see the various kinds of network available in the corporate world and their benefits.
LAN LAN stands for Local Area Network. These networks can consist of anywhere from two to thousands of computers. Even a simple network of one computer connected to one printer can be considered a LAN. Normally, LAN is a computer network that spans a relatively small area. Most
LANs are confined to a single building or group of buildings. However, one LAN can be connected to other LANs over any distance via telephone lines and radio waves.
Most LANs connect workstations and personal computers. Each node (individual computer) in a LAN has its own CPU with which it executes programs, but it also is able to access data and devices anywhere on the LAN. This means that many users can share expensive devices, such as laser printers, as well as data. Users can also use the LAN to communicate with each other, by sending e-mail or engaging in chat sessions.
LANs are capable of transmitting data at very fast rates, much faster than data can be transmitted over a telephone line; but the distances are limited, and there is also a limit on the number of computers that can be attached to a single LAN.
Peer-to-Peer - Sometimes called P2P, these networks are the simplest and least expensive networks to set up. P2P networks are simple in the sense that the computers are connected directly to each other and share the same level of access on the network, hence the name. Computer 1 will connect directly to Computer 2 and will share all files with the appropriate security or sharing rights. If many computers are connected a hub may be used to connect all these computers and/or devices. The diagram below shows a simple peer-to-peer network:
A peer-to-peer network is sometimes the perfect (and cheap) solution for connecting the computers at a small nonprofit. However, peer-to-peer networking has its limitations, and your organization should tread with caution to avoid headaches (security issues, hardware inadequacies, backup problems, etc.) down the road.
Client/Server - Probably the most common LAN types used by companies today, they are called "client/server" because they consist of the server (which stores the files or runs applications) and the client machines, which are the computers used by workers. Using a client/server setup can be helpful in many ways. It can free up disk space by providing a central location for all the files to be stored. It also ensures the most recent copy of that file is available to all. A server can also act as a mail server (which collects and sends all the e-mail) or a print server (which takes all the print jobs and sends them to the printer, thus freeing computing power on the client machine to continue working).
Establishing the right kind of network for your organization is important to make the most of your time and money. While a peer-to-peer network is often a good choice for small networks, in an environment with more than 10-15 computers, a peer-to-peer network begins to become more trouble than it is worth: your computers start to slow down, you can never find the file you are looking for, and security is non-existent. If this is happening in your organization, it is probably time to switch to a client-server network by bringing in a dedicated server to handle the load. The server is called "dedicated" because it is optimized to serve requests from the "client" computers quickly. The diagram below shows a simple client-server network:
What is a server?
A server is simply a computer that is running software that enables it to serve specific requests from other computers, called "clients." For example, you can set up a file server that becomes a central storage place for your network, a print server that takes in print jobs and ships them off to a printer, as well as a multitude of other servers and server functions. A server provides many benefits including:
• Optimization: server hardware is designed to serve requests from clients quickly
• Centralization: files are in one location for easy administration
• Security: multiple levels of permissions can prevent users from doing damage to files
• Redundancy and Back-up: data can be stored in redundant ways making for quick restore in case of problems
The client-server model of networking is the way to go for larger organizations. Once you have a client-server network set up, it should provide you with more flexibility than a peer-to-peer network as your needs change.For example, as network traffic increases, you can add another server to handle the additional load. You can also consider spreading out tasks to various servers, ensuring that they are performed in the most efficient manner possible. Most importantly, a client-server network is much easier to secure and back up, greatly improving the reliability and confidentiality of your data.
Wireless Networking
Wireless networking products have become more popular in the last few years due to an increase in competition among manufacturers and the emergence of a more dominant wireless technology standard. This section looks at the benefits and drawbacks of wireless networking and provides further resources for research into wireless products. Wireless networking refers to hardware and software combinations that enable two or more appliances to share data with each other without direct cable connections. Thus, in its widest sense, wireless networking includes cell and satellite phones, pagers, two-way radios, wireless LANs and modems, and Global Positioning Systems (GPS).
Wireless LANs
Wireless LANs enable client computers and the server to communicate with one another without direct cable connections. Generally, a wireless LAN is connected to an existing wired LAN, although they can exist without a wired LAN (in this case, users will only be able to communicate with other users on the same subnet).
Necessary components include an access point, Client LAN adaptors and the wired LAN. The access point is a device that translates between the wired LAN and the wireless LAN. The Client LAN Adaptors are PC cards, PCI or ISA boards that plug into laptop or desktop computers equipped with radio transceivers to communicate with the Access point. Other components to a wireless LAN can include Extension Points and Directional Antennas. Extension Points are devices similar to the access point, but not connected to the wired LAN. Extension points serve to extend the range of the wireless network by relaying signals from client computers to the Access point. Directional Antennas serve to connect wireless networks located at a greater distance from one another. Each network would have an antenna targeted at each other (known as a "line of site" connection).
How a Wireless LAN works?
In a typical wireless LAN configuration, the access point connects to the wired network from a fixed location using standard cabling. The access point receives and transmits data between the wireless LAN and the wired network infrastructure. A single access point can support a small group of users and can function within a range of less than one hundred to several hundred feet. End users access the wireless LAN through the wireless-LAN adapters installed in their computers.
Benefits of Wireless LANs
Cost: Wireless LANs can cost less to implement than wired LANs, especially in situations where implementing a wired LAN requires extensive labor and materials to install the wiring and drops. For environments that are difficult to wire (such as schools or temporary spaces) a wireless network can be more cost-effective in the long run than a wired one.
Simple/flexible to Install: Wireless LANs eliminate the time needed with wired LANs for laying and pulling wires, and can reach places that cannot be reached by wires.
Portability: Wireless LAN systems can move physical locations much easier than wired LANs, reducing total cost of ownership for organizations that are on the move.
Mobility: Wireless LAN systems can provide LAN users with access to network information anywhere in their organization.
Scalability: Wireless LAN systems can be configured for small offices and large, with peer-to-peer systems or large established LANs, specific to the localized need of a workgroup or across the whole enterprise. Wireless LAN systems grow easily with the need by adding more access points, client LAN adaptors and extension points. Wireless can be a good solution if you need to connect several buildings without installing a wired connection. Wireless LAN bridges can extend LANs that are typically one to five miles apart. These wireless bridges span multiple-building LANs without incurring the monthly costs of a T1 or higher speed lines.
Drawbacks of Wireless LANs
Cost: In environments with installed wiring or less demanding wiring needs, the up front costs of adopting a wireless LAN system can be more expensive than with wired LANs.
Interoperability: There are several competing technologies used by wireless LAN vendors to communicate data between hardware, with no ability for communication directly between systems using these different standards.
Interference: Most of the wireless devices today operate on 2.4-GHz radio bands, which are also used by cordless phones and most microwave ovens. The potential for interference when used near other devices sharing the same frequency band
Speed: Most commonly used wireless LAN products are rated for a maximum 11Mbps throughput, and in practice see speeds about 80% less than this - some wireless LAN products are rated for speeds much less than this (HomeRF systems for example). Still quite speedy for most network needs and for broadband Internet sharing, but for larger offices with high network traffic and demands for speed, this should be taken into consideration.
Wide Area Networks (WANs)
Wide Area Networks or WANs are very large networks of computers. These networks span large geographical areas, generally covering a couple miles, sometimes connecting computers thousands of miles apart. A WAN can also be a collection of LANs, bringing together many smaller networks into one large network. A WAN can constitute a very large corporate or government network, spanning the country or even the world. In fact, the Internet is the largest and most common WAN in existence today.
Normally, it means a computer network that spans a relatively large geographical area. Typically, a WAN consists of two or more local-area networks (LANs).
Computers connected to a wide-area network are often connected through public networks, such as the telephone system. They can also be connected through leased lines or satellites. The largest WAN in existence is the Internet.
Controller Area Network (CANs)
Last modified:
Abbreviated CAN, a serial bus network of microcontrollers that connects devices, sensors and actuators in a system or sub-system for real-time control applications There is no addressing scheme used in controller area networks, as in the sense of conventional addressing in networks (such as Ethernet). Rather, messages are broadcast to all the nodes in the network using an identifier unique to the network. Based on the identifier, the individual nodes decide whether or not to process the message and also determine the priority of the message in terms of competition for bus access. This method allows for uninterrupted transmission when a collision is detected, unlike Ethernets that will stop transmission upon collision detection.
Controller area networks were first developed for use in automobiles. Equipped with an array of sensors, the network is able to monitor the systems that the automobile depends on to run properly and safely. Beyond automobiles, controller area networks can be used as an embedded communication system for microcontrollers as well as an open communication system for intelligent devices.
The controller area network, first developed by Robert Bosch in 1986, is documented in ISO 11898 (for applications up to 1 Mbps) and ISO 11519 (for applications up to 125 Kbps).
Campus Area Networks (CANs)
An interconnection of local-area networks within a limited geographical space, such as a school campus or a military base
Metropolitan Area Networks (MANs)
Last modified: Tuesday, February 03, 2004
A data network designed for a town or city. In terms of geographic breadth, MANs are larger than local-area networks (LANs), but smaller than wide-area networks (WANs). MANs are usually characterized by very high-speed connections using fiber optical cable or other digital media.
Virtual Private Network (VPNs)
Answer: A virtual private network (VPN) is a private data network that makes use of the public telecommunication infrastructure, maintaining privacy through the use of a tunneling protocol and security procedures. A virtual private network can be contrasted with a system of owned or leased lines that can only be used by one company. The idea of the VPN is to give the company the same capabilities at much lower cost by using the shared public infrastructure rather than a private one.
A VPN connects computers located at various places throughout a city, a state, or even globally. It provides a secure network connection for distance computers and does not require laying cable to supply the connection. You can set up a VPN yourself (Windows 2000 server has settings to establish a VPN) or you can purchace one as a service from another company.
Home Area Network (HANs)
A HAN is a network contained within a user's home that connects a person's digital devices, from multiple computers and their peripheral devices to telephones, VCRs, televisions, video games, home security systems, "smart" appliances, fax machines and other digital devices that are wired into the network.
An Introduction to Wireless Networks for the Small/Medium Enterprise (SME)
Wireless Networking, WiFi, is not a new technology, but it is only recently that it has become mainstream. What are the benefits of wireless networks and should you be considering using it?
The advent of portable computing devices is one of the main drivers for the adoption of wireless networking. Today, around 50% of new laptops come wireless enabled out of the box. All of Apple's latest line of laptops comes with both wireless & bluetooth built in. Many Microsoft Windows laptops are similarly wireless enabled.
A powerful alliance of vendors joined together in 1999 to form the WiFi Alliance. You can be assured that any device approved by the WiFi Alliance will interoperate happily with any other approved device. The term WiFi has become corrupted in common usage to mean wireless networks in general, not just devices approved by the WiFi alliance.
Why adopt WiFi?
Today's workforce, equipped with PDAs, laptops and other mobile devices, demand access to your network from wherever they are, without the hassle of a fixed network. WiFi allows your business to deploy a network more quickly, at lower cost, and with greater flexibility than a wired system.
Productivity increases too, since workers can stay connected longer, and are able to collaborate with their co-workers as and where needed.
WiFi networks are more fluid than wired networks. A network is no longer a fixed thing, networks can be created and ripped down in an afternoon instead of the days or weeks required to create a structured cable network.
Architecture
Wireless cards can operate in two modes, Infrastructure and Ad-hoc.
Most business systems use wireless in Infrastructure mode. This means that devices communicate with an access point. Typically the access point also has a connection to the company wired network, allowing users access to servers and files as if they were physically attached to the LAN.
Ad-hoc connections are direct connections between wireless cards. This type of connection is more common amongst home users, but if used by business users could have serious management and security implications.
Management
You can easily connect to a WiFi network anywhere within range of an access point. This is a boon for your workers, but unfortunately, it also brings with it a few headaches for the IT department.
Security
Security is the bane of everybody who puts together a wireless network. access points, using factory default settings, are not secure at all. So, if security is such a concern does that mean I shouldn't deploy WiFi? No, it doesn't. But it is something that you should bear in mind when in the planning stage.
When talking about security there is no such thing as having a completely secure system. Everything is insecure to some degree or other. The degree of security you require is dictated by the sensitivity of the information you possess.
If you require very high levels of security then you cannot rely on the built in security measures of a WiFi network alone. On the other hand, most small to medium sized companies do not require very high levels of security.
Integrating Enterprise Information on a Global Scale
In today's challenging business environment, companies are encountering levels of growth and change that can quickly make their business information systems obsolete. These enterprises are meeting this challenge by implementing real-time transaction processing systems to reduce cycle time, cut operation costs, and improve responsiveness to corporate users, customers, and vendors alike.
This section highlights the key factors that an organization must address when building a globally integrated business system. It also describes how 3Com Corporation implemented its own state-of-the-art enterprise resource planning (ERP) system using SAP R/3 business application solutions, the Informix OnLine Dynamic Server relational database, and 3Com's own networking systems and products. In addition, the paper touches on the advantages that the partnership between 3Com and Informix offers networking customers.
Thriving in a Volatile Business Climate
Many industries today are characterized by fierce competition, intense time-to-market pressure, and consolidation through mergers and acquisitions. Companies depend on their transaction processing systems to maintain a competitive edge, and to sustain business models that must constantly adapt to changing market conditions.
11.602 © Copy Right: Rai University 226 Management Information Systems
An effective business system is a marriage between information system (IS) and business process. When laying out a strategic plan and defining the underlying architecture for a new corporate transaction processing system, most organizations seek to achieve these primary objectives:
• Make business operations more responsive to customers and the needs of the enterprise by integrating logistical data into one global system
• Implement real-time transaction processing to provide online information access anytime, anywhere
• Develop processes that reduce cycle time for order fulfillment and minimize inventory and distribution costs
• Design a future-proof solution that can scale easily to accommodate growth
• Leverage technology to reduce long-term IS costs
Information technology has progressed dramatically in the last few years. It is now possible to integrate diverse functions more fully using software that offers better price/performance as well as plug-and-play modularity. The latest technology also makes it possible to combine data in a scalable, high-performance relational database, and to transmit the information globally over a reliable high-speed network.
A business information system may be divided into three major elements: the ERP applications, the database, and the network configuration. Each of these elements is equally important, and all of them must mesh smoothly to ensure a successful implementation.
Success Factors Here are some key factors that can help ensure successful implementation of a large-scale business system:
1. Keep the network as flat as possible for simplicity and efficiency. Utilize switching for high performance where you can, and use routing where you must at the network's edges and where security is a key issue.
2. Resist the tendency to over design; you cannot cost-effectively design a completely fail-proof network. Rather, design the network so that a failure in one area will not impact the business processes across the entire enterprise.
3. Put all application and database servers on their own Domain Name Service. This will avoid single points of failure. Again, keep the applications environment as flat as possible.
4. Involve the network management organization as a peer member on the business system implementation team from the beginning. Application management and bandwidth management are both important.
5. Commit to extensive training for users and managers. In-depth training early in the process will minimize the negative impact on productivity of introducing a new system.
6. Engage a consultant to ensure successful implementation. 3Com benefited greatly from Price Waterhouse's experience in R/3 implementations.
7. Conduct stress testing up front. Be prepared for constant refinement of baselines.
How does Management use Information?
The Management Process
Determining how management uses information may be done best in the context of the management process, which is a cycle consisting of the following stages:
Planning |
setting goals and objectives and determining specific courses of action by which they may be attained |
Organizing |
identifying resources required to carry out a plan |
Staffing |
acquiring resources (e.g., recruiting personnel, purchasing material, raising capital) |
Coordinating |
executing the plan (e.g., giving instructions, allocating resources) |
Controlling |
ensuring that actual performance meets planned performance and making changes to plans and/or resource allocations to correct discrepancies |
|
|
Information is necessary in all of these stages.
When setting goals and objectives, analysis of historical data can help to predict future trends. Best/worst/average case analyses can aid in the making of decisions where a choice must be made between alternative courses of action. There are also several modelling techniques, such as trend analysis and linear programming, which may be used to optimize production schedules and facility locations and to solve other similar problems - if enough information is available to determine and quantify cause-and-effect relationships between factors and results.
Identifying resource requirements for a completely unfamiliar plan may be little more than educated guesswork. However, in many cases, several parts of a plan are similar to, if not identical to, parts of past plans. Searching of historical data may identify solutions to past problems which are applicable to current problems. Also, certain financial models can be used to identify sources of capital.
Staffing
Again, historical records can be useful in acquiring resources. Information on qualified personnel already within the organization or reliable suppliers can substantially ease the task of locating them. There is a drawback, though, to reliance on this method of staffing in that it may preempt the location of new resources, such as the development of new business contacts or the hiring of talented new employees. To find external information, research is required.
A large part of coordination is communication. Information and instructions flow downward through the organization, communicating the nature of tasks to be performed, the materials to be used, and the destination of goods or the recipients of services. The analytical methods used in planning may also be applied to coordinating, but on a shorter term basis. The relationship between planning and coordinating can be represented this way: as planning becomes shorter and shorter in term, it approaches immediacy and eventually turns into execution.
The need for information at this stage is obvious. In order to compare actual performance to planned performance, information on actual performance is required. This information may include records of resource consumption, results of quality inspections, the disposition of output goods and services, and status reports on the accomplishment of tasks. These can then be compared against the standards established during planning. If discrepancies in performance are found, data analysis can pinpoint the source of the discrepancies so that corrective measures can be taken.
Certainly, not all activities are effectively supported by historic and current internal information alone. For example, staffing can require external information. Also, the planning activities of top executives may depend on a "feel" for the industry - an intuitive sense of the environment - which can only be gained from information that is more eclectic (i.e., not easily quantifiable) than is within the scope of an MIS to maintain. Other tasks are very well supported by computerized information systems. Controlling, for example, is enormously aided by such a system's ability to supply current information quickly and to update information quickly.
Process and Hierarchy
The degree to which many tasks can be supported by an MIS depends on the level of management. Between levels, there are differences not only in the type and scope of activities, but also in the amount of time spent on different stages of the management process. An approximate breakdown of how different levels of management spend their time (Figure 1) shows that the most time-consuming tasks of top and first-line management are planning and coordinating, respectively, and that middle management's time is dominated by planning and controlling. The information needs of different levels of management will be different.
Figure 1. Comparison of management time allocation (Kroeber 103)
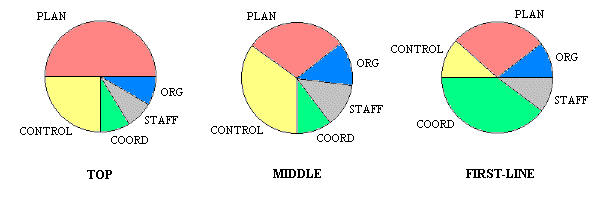
First-line management is mostly concerned with operational decision-making, such as inventory control, equipment maintenance, and employee evaluation. First-line managers may not need MIS services at all if they are in regular contact with actual production. Any decisions they make which can be supported by computerized systems tend to be straightforward enough that they can be completely automated so that they require no human intervention.
Middle management is involved in tactical decision-making - deciding how best to carry out plans. Examples of tactical decisions include resource allocation, production scheduling, and forecasting. Middle managers need information on operations, in correspondence with their heavy role in controlling. They make more structured decisions which require basically the same types of information on a regular basis.
Top level managers are involved in strategic decision-making - directing the business to gain a competitive edge. They make decisions such as capital budgeting, product line, and mergers and acquisitions. Top managers will want to see "the big picture," information on larger influences both in- and outside of their particular businesses. They need summarized, meaningful information to help them visualize the business without losing the ability to examine details should the need arise. The decisions they make are intuitive and creative, and as a consequence their information needs are difficult to anticipate.
Analyzing Methods of Information Delivery
Scheduled Reporting
In the beginning, computer systems were not the powerhouses that they are today. They could not support the load of several simultaneous interactive users without serious performance degradation. Also, they were not nearly as user-friendly as today's computers with their slick graphical user interfaces and point-and-click mouse capabilities. The people who knew how to use computers had to be specialized. Managers, some of whom did not even know how to type, had to rely on those who had technical expertise to use the systems to deliver the information to them. This fact, and the influence of traditional methods of reporting developed before the advent of computerized MIS, is the probable reasons for the continuing present predilection towards paper reports as the primary form of information delivery. Although some systems have evolved to the point where reports are distributed through email rather than through slower interoffice mail, the principle remains the same: someone else, usually the MIS department, pre-packages the information and gives it to the user.
Reports are good for presenting predefined information in a structured and relatively attractive way. Since they are predefined, they can be automated. They provide the same information regularly; and if they are well-designed, they are a simple and familiar method of communicating information. This method of information delivery can be ideal for controlling and keeping track of continuing developments.
If the reports are not well-designed, they can be a nightmare. Databases can store an excruciating amount of information at an excruciating level of detail which no one particularly wants to see.
The main advantage to regularly scheduled reporting is that they require relatively little effort for either side to produce and use, after the initial design process. The main disadvantage is their lack of flexibility. Middle management may find this method of information delivery satisfactory for limited purposes. Some flexibility may be incorporated by allowing users to choose from a selection of reports and report formats, but it remains tedious to obtain additional information.
Ad Hoc Interactive Querying
Now that interactive computing by many simultaneous users is technologically feasible, it is possible to implement systems where users have direct online access to databases and information. Software tools and security systems have been designed to enable users to query and manipulate data and to create their own reports. With this type of system, information needs of controlling and coordinating can still be supported; and higher level planning and organizing, for which information needs are not easy to anticipate, can be better supported.
Flexibility comes with a price: it increases the burden on the user to understand the data and the access tools. Some managers find that working with data helps them to understand the business better and increases their creativity and productivity because they can explore an idea quickly without submitting a request for information. Other managers find that the access tools are too complicated and cumbersome for occasional use, or that they waste too much time fighting the computer and doing what the MIS department should be doing. Some managers are willing to take courses or spend their own time to learn software; some are not. Much depends on the interface which is presented to the user.
Some very powerful and attractive software packages are commercially available. These packages can integrate several different types of databases, link information tables to create customized tables, sort, calculate, filter, format output, generate graphs, link to other applications, and build accessory applications. The range of options can overwhelm the casual user. Even if training is provided, adeptness at using the tool comes only from frequent and extensive use. More limited in-house software packages designed to work with existing systems are less flexible, but their simplicity is less intimidating.
Some possible solutions to the problem of trading flexibility for ease of use might be for the MIS department to customize the interfaces of the more powerful access tools or to train certain people in the more powerful access tools and attach them as a mini-MIS department to certain management teams or top executives. They would customize the interfaces for the managers and make changes according to their specifications. However, there would still be delays and misunderstandings of specifications. The advantages of using more powerful tools may not justify the cost of adapting the applications and making them compatible with existing systems.
Ad hoc querying allows users faster and more direct access to information and greater determination over the information they see. Users can search for information even if they cannot articulate exactly what they are looking for. However, the effectiveness of the system depends largely on the the effectiveness of the users. The best that the MIS department can do is survey the users and try to supply them with tools that they will use effectively.
Data analysis is defined as the examination of subsets of data in order to discern hidden information (Kroeber 110). Many planning and coordinating activities, especially those of middle management, are aided by mathematical models. Sometimes, analysis is as simple as subtotalling certain data fields or graphing data to make patterns more visible. Complex mathematical models may be slightly outside of a mandate of information storage and delivery, but analysis is an integral part of decision making and may be easily enhanced by computerized systems. Simple summarization functions can be built into access and report generation tools. Common models, calculations, and if-then case analyses can be stored as templates in common repositories.
As with database accessing software, software used for data analysis, such as spreadsheets, can range from very powerful to very basic. As well, the same problems of usability versus flexibility are associated. The MIS department can provide training, but it cannot force people to use systems they are not comfortable with. In this situation, though, it is more feasible to hire experts to use the software because the requirements are more specific and rigid. The experts can create and run analytical models and report results back to management. It is up to management to decide a course of action based on the results.
Realistically, it is impossible for an MIS to support all management activities: they are too diverse and unquantified. However, an MIS can concentrate on improving its support of activities that are well supported, thus freeing managers to perform those activities that cannot be facilitated by an MIS. It can be seen that the structured activities of middle management are most easily supported. Middle managers are likely to be the most frequent users of an MIS, so planning should focus on their needs.
The best method of information delivery depends on how much the users want to see balanced against how much they are willing to do. For some uses, scheduled reporting may be ideal. However, the advantages of ad hoc querying over restrictive reporting are too great to ignore. Eventually, an MIS department must try to expand its usefulness by increasing the range of data and informative options available to users. The flexibility of ad hoc querying is necessary to increase the functionality of an MIS.
Information Systems in the Enterprise
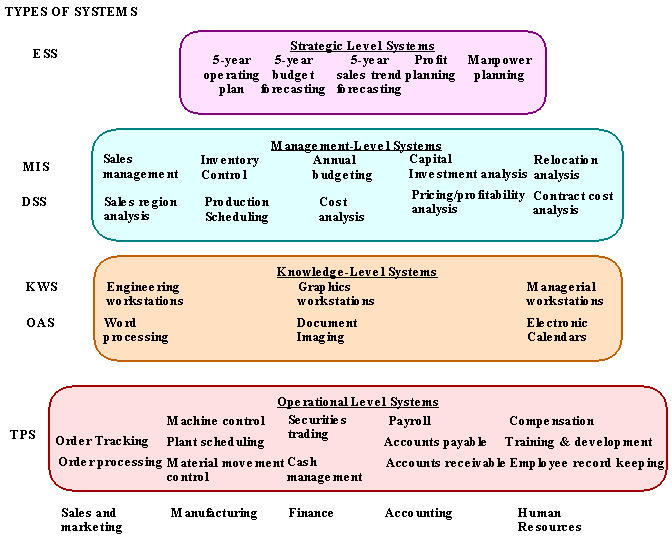
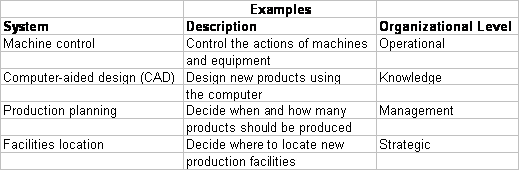
KINDS OF INFORMATION SYSTEMS
Four General Kinds of IS
Support operational managers by monitoring the day-to-day’s elementary activities and transactions of the organization. e.g. TPS.
Support knowledge and data workers in designing products, distributing information, and coping with paperwork in an organization. e.g. KWS, OAS
Support the monitoring, controlling, decision-making, and administrative activities of middle managers. e.g. MIS, DSS
Support long-range planning activities of senior management. e.g. ESS
A Framework for IS
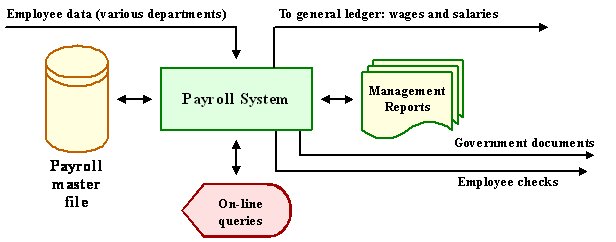
Transaction Processing Systems (TPS)
Computerized system that performs and records the daily routine transactions necessary to conduct the business; these systems serve the operational level of the organization
A Symbolic Representation for a payroll TPS
Office Automation Systems (OAS)
Computer system, such as word processing, electronic mail system, and scheduling system, that is designed to increase the productivity of data workers in the office.
EXAMPLE: document imaging system
Knowledge Work Systems (KWS)
Information system that aids knowledge workers in the creation and integration of new knowledge in the organization
EXAMPLE: Engineering workstations
Decision Support Systems (DSS)
Information system at the management level of an organization that combines data and sophisticated analytical models or data analysis tools to support semi-structured and unstructured decision making
EXAMPLE: sales region analysis
Characteristics of Decision-Support Systems
DSS offer users flexibility, adaptability, and a quick response.
DSS operate with little or no assistance from professional programmers.
DSS provide support for decisions and problems whose solutions cannot be specified in advance.
DSS use sophisticated data analysis and modelling tools.
Characteristics of Management information Systems
MIS support structured decisions at the operational and management control levels. However, they are also useful for planning purposes of senior management staff.
MIS are generally reporting and control oriented. They are designed to report on existing operations and therefore to help provide day-to-day control of operations.
MIS rely an existing corporate data-and data flows.
MIS have little analytical capability.
MIS generally aid in decision making using past and present data.
MIS are relatively inflexible.
MIS have an internal rather than an external orientation.
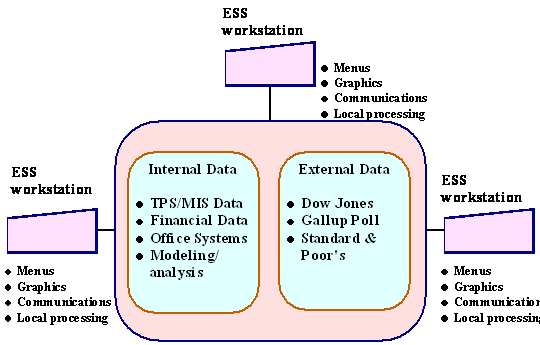
Executive Support Systems (ESS)
Information system at the strategic level of an organization that address unstructured decision making through advanced graphics and communications.
TYPE: Strategic level
EXAMPLE: 5 year operating plan
Model of a Typical Executive Support System
Major Types of Information Systems
Classification of IS by Organizational Structure
Departmental Information Systems
Enterprise Information System
Inter-organizational Systems
Classification of IS by Functional Area
The accounting information system
The finance information system
The manufacturing (operations, production) information system
The marketing information system
The human resources information system
Sales & Marketing Systems
Systems that help the firm identify customers for the firm’s products or services, develop products and services to meet customer’s needs, promote products and services, sell the products and services, and provide ongoing customer support.

Manufacturing and Production Systems
Systems that deal with the planning, development, and production of products and services and with controlling the flow of production
Finance and Accounting Systems
Systems that keep track of the firm’s financial assets and fund flows

Human Resources Systems
Systems that maintain employee records; Track employee skills, job performance, and training; and support planning for employee compensation and career development.

Examples of Business Processes

Customer Relationship Management
Customer relationship management Business and technology discipline to coordinate alt of the business processes for dealing with customers.
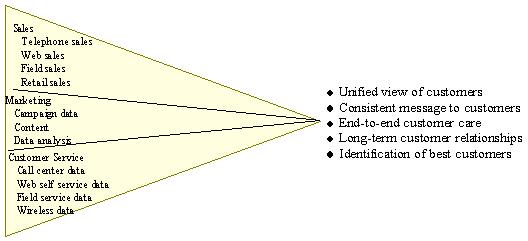
Customer Relationship Management
Supply chain management Integration of supplier, distributor, and customer logistics requirements into one cohesive process.
Supply chain Network of facilities for procuring materials, transforming raw materials into finished products,' and distributing finished produce to customers
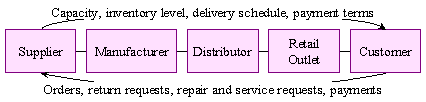
HOW INFORMATION SYSTEMS CAN FACILITATE SUPPLY CHAIN MANAGEMENT
Information systems can help participants in the supply chain:
Decide when and what to produce, store, and move
Rapidly communicate orders Track the status of orders
Check inventory availability and monitor inventory levels
Track shipments
Plan production based on actual customer demand
Rapidly communicate changes in product design
Provide product specifications
Share information about defect rates and returns
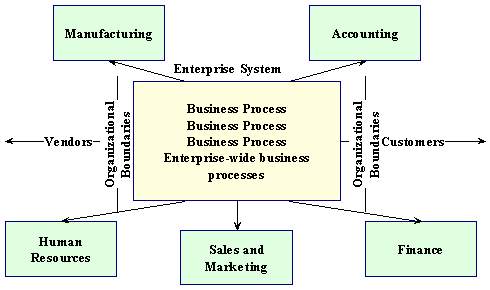
Enterprise Systems
Firm wide information systems that integrate key business processes so that information can flow freely between different parts of the firm
Traditional View of Systems
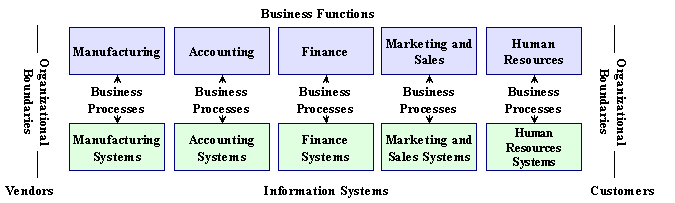
Enterprise Systems
Benefits and Challenges of Enterprise Systems
Firm structure and organization: One Organization
Management: Firm wide Knowledge-based Management Processes
Technology: Unified Platform
Business: More Efficient Operations and Customer-driven Business Processes
Daunting Implementation
High Up-front Costs and Future Benefits
Inflexibility
Challenges in Management of Information Systems
Although information systems are creating many exciting opportunities for both businesses and individuals, they are also a source of new problems, issues and challenges for managers. In this course, you will learn about both the challenges and opportunities information systems pose, and you will be able to use information technology to enrich your learning experience.
New Opportunities with Technology
Is this new technology worth the headaches and heartaches associated with all the problems that can and will arise? Yes. The opportunities for success are endless. The new technologies do offer solutions to age-old problems. Improvements are possible to the way you operate and do business.
The rest of the lessons in this book and this course will give you tools you can use to be successful with the current and future Management Information Systems.
The Strategic Business Challenge
Companies spend thousands of dollars on hardware and software, only to find that most of the technology actually goes unused. "How can that be?" you ask. Usually because they didn't pay attention to the full integration of the technology into the organization Merely buying the technology without exploiting the new opportunities it offers for doing business smarter and better doesn't accomplish much. Think and rethink everything you do and figure out how you can do it better. Change is inevitable, and information must be managed just as you would any other resource.
Creating a digital firm and obtaining benefit is a long and difficult journey for most organizations. Despite heavy information technology investments, many organizations are not realizing significant business value from their business systems, nor or they become digitally enabled. The power of computer hardware and software has grown much more rapidly than the ability of organizations to apply and to use this technology. To fully benefit form information technology, realize genuine productivity, and take advantage of digital firm capabilities, many organizations actually need to be redesigned. They will have to make fundamental changes in organizational behavior, develop new business models and eliminate the inefficiencies of outmoded organizational structures. If organizations merely automate what they are doing today, they are largely missing the potential of information technology.
The Globalization Challenge
The world becomes smaller every day. Competition increases among countries as well as companies. A good Management Information System meets both domestic and foreign opportunities and challenges. The rapid growth in international trade and the emergence of a global economy call for information systems that can support both producing and selling goods in many different countries. In the past, each regional office of a multinational corporation focused on solving its own unique information problems. Given language, cultural and political differences among countries, this focus frequently resulted in chaos and the failure of central management controls. To develop integrated, multinational, information systems, businesses must develop global hardware, software and communication standards; create cross-cultural accounting and reporting structures; and design transnational business processes.
The Information Architecture Challenge
You have to decide what business you are in, what your core competencies are, and what the organization's goals are. Those decisions drive the technology, instead of the technology driving the rest of the company. Purchasing new hardware involves more than taking the machine out of the box and setting it on someone's desk. Remember the triangle of hardware, software, Take care of the people and they will take care of the rest! Information architecture describes how to incorporate technology into the mainstream processes in which the business is involved. How will the new Information System support getting the product produced and shipped? How will Advertising and Marketing know when to launch ad campaigns? How will Accounting know when to expect payment?
Many companies are saddled with expensive and unwieldy information technology platforms that cannot adopt to innovation and change. Their information systems are so complex and brittle that they act as constraints on business strategy and execution. Meeting new business and technology challenges may require redesigning the organization and building a new information architecture and information technology infrastructure.
The Information Systems Investment Challenge
Too often managers look at their technological investments in terms of the cost of new hardware or software. They overlook the costs associated with the non-technical side of technology. Is productivity up or down? What is the cost of lost sales opportunities and lost customer confidence from a poorly managed E-Business Web site? How do you determine if your Management Information System is worth it?
A major problem raised by the development of powerful, inexpensive computers involves not technology but management and organizations. It’s one thing to use information technology to design, produce, deliver and maintain new products. It’s another thing to make money doing it. How can organizations obtain a sizeable payoff from their investments in information systems? How can management make sure that the management information systems contribute to corporate value?
The Responsibility and Control Challenge
Remember, humans should drive the technology, not the other way around. Too often we find it easier to blame the computer for messing up than to realize it's only doing what a human being told it to do. Your goal should be to integrate the technology into the world of people. Humans do control the technology, and as a manager, you shouldn't lose sight of that.
How can we define information systems that people can control and understand? Although information systems have provided enormous benefits and efficiencies, they have also created new problems and challenges of which managers should be aware.
The following table describes some of these problems and challenges.
Positive and Negative Impacts of Information Systems
Benefits of Information Systems |
Negative Impact |
Information system can perform calculations or process paperwork much faster than people. |
By automating activities that were previously performed by people, information systems may eliminate jobs |
Information systems can help companies learn more about the purchase patterns and the preferences of the customers. |
Information systems may allow organizations to collect personal details about people that violate their privacy |
Information systems provide new efficiencies through services such as automated teller machines (ATMs), telephone systems, or computer controlled airplanes and air terminals |
Information systems are used in so many aspects of everyday life that system outages can cause shutdowns of businesses or transportation services, paralyzing communities. |
Information systems have made possible new medical advances in surgery, radiology, and patient monitoring |
Heavy uses of information systems may suffer repetitive stress injury, techno stress, and other health problems |
The internet distributes information instantly to millions of people across the world. |
The internet can be used to distribute illegal copies of software, books, articles, and other intellectual property. |
Management's focus must continually change to take advantage of new opportunities. Changes should take place throughout the organization. They require lots of attention and planning for smooth execution.
Extranets pack tough new challenges for MIS - Industry Trend or Event
Asking analysts and consultants to talk about the extranet phenomenon often leads to the same response: "What do you mean when you say extranet?" Confusion abounds when it comes to trying to nail down a solid definition for something that to some folks makes more sense as a concept than as a product or service.
In fact, at least one industry player believes the term to be meaningless. Semantics aside, many organizations are beginning to see real advantages to allowing selected suppliers, customer and business partners access to part or all of their own networks via the Internet, according to observers. Within the next three to four years, "the primary vehicle for delivering electronic commerce in the b-to-b [business to business] world will in fact be over extranets, rather than private value-added networks or even the global, open Internet," says Alyse Terhune, a research director with the Gartner Group in Stamford, Conn. And while companies used to develop and implement their own extranet strategies, more and more are looking to outside help, according to analysts. Internet Service Providers (ISPs) are particularly eager to cash in on the growing market.
Outsourcing may be a cheap and easy answer for some firms, but Terhune isn't convinced it's a surefire strategy. "I think that there are lots of pieces involved in a successful extranet, and some of them are the core competency of ISPs and some of them aren't." A solid infrastructure is one thing, she says, but administrative logistics can be something else entirely. Especially when different organizations with different ways of doing business get together
You have to deal with the business process that's being accommodated. That means providing things like applications that will facilitate say, buying and selling. That's more than just a catalogue. In the business world that's who within my requisitioning organization can buy from what suppliers," what they can buy and how much they can buy, she says.
Security can also be a big issue, but is more of an administrative problem than a technological one, says Terhune. "When you really look at the problem of securing information and determining which information has to be secured and to whom, it becomes more complicated." Technical solutions such as encryption, firewalls and data packets are "more or less standard features" these days, Reisman claims, but some organizations are still very Internet-shy.
Large corporations tend to be bigger targets for hackers and spies, he says, something small firms might want to consider when budgeting for security features. Future developments are particularly hard to quantify when it comes to extranets. It's difficult enough to come to a consensus on what they are now, let alone to guess how they might develop or grow in use over time.
Managers will also be faced with ongoing problems of security and control. Information systems are so essential to business, government and daily life that organisations must take special steps to ensure that they are accurate, reliable and secure. A firm invites disaster if it uses systems that don’t work as intended, that don’t deliver information in a form that people can interpret correctly and use, or that have control rooms, where control don’t work or where instruments give false signals. Information systems must be designed so that they function as intended and so that humans can control the process.
Electronic Conferencing
Professionals in all fields are looking to Internet technology to find communication methods that encourage greater collaboration and are an efficient way of dispersing helpful and relevant information in a cost effective manner. One method that has become increasingly popular is conferencing, whether it be on “electronic bulletin
Boards”, listservs, in chat rooms or using web-based meeting protocols
Conferencing allows a large group to exchange ideas by reading and posting messages which are delivered to a central point and broadcast to the conference participants by special software. This is done in a synchronous or asynchronous mode, that is when all participants gather together at the same time or not! i.e. that conference participants can read ad post messages at any time.
Conferencing has its advantages and disadvantages. By far, it is cheaper than using long-distance telephone or fax and the software and hardware needed to run it, a personal computer and an Internet connection, are becoming so readily available that it makes it possible for larger numbers of people to become participants. Conferencing keeps meeting costs down because the costs associated with face-to-face meetings such as travel and accommodations don’t exist. And in most modes of Internet conferencing, subscribers can participate at a time that is convenient for them, thus helping in the old “time management” dilemma.
Some people find it difficult to commit the amount of time it takes to make conferencing successful, and others don’t like it because of the lack of personal contact. Participation is linked to a person’s previous experience with technology and the Internet, his likes and dislikes or her preferred learning styles. Research suggests that auditory learners may feel distanced from discussions in asynchronous conferences and may prefer telephone or face-to-face meetings where they can be heard. Visual learners usually flourish in the on-line environment because they are used to processing large amounts of information in this manner.
• Pre-planning: Decide on a series of topics and find guest facilitators/moderators who will lead the discussion on a given topic. Determine how long a conference will last--a day, a week, several weeks, a month etc. Spread the dates of the conferences out over a six or eight month period with a good break between conferences (three conferences in this time period would be good). Promote the conferences in advance. This allows people to begin thinking about the topics and the kinds of questions they would like to ask or information they would like to share.
• Promotion: Begin sending messages introducing the moderator, giving information about the participants and commenting on different elements of the topic to conference subscribers two weeks before the conference to build anticipation.
• Introductions: Ask the guest moderator to introduce him/herself a week or so before the actual start of the conference. During that time, ask the moderator to post the conference agenda and request potential participants to: a) introduce themselves, b) suggest what they'd like to learn from the conference, and c) identify one or two of their favourite resources related to the topic. These are ways to “break the ice” that can contribute to the quality of the conference and, unobtrusively, help the participants feel more comfortable as they get to know and feel at ease with each other and this, for some of them, new manner of meeting.
• Time Factor: Consider stretching the conference out over an appropriate period of time and have the moderator post her/his “conference” material every third day or so, depending on the over all length of the conference, to give participants more time to come and go on the system. Adjust this as time goes on, as participants become more comfortable with this process in general and become more active in their participation.
• Be Prepared: There will be lulls in the action: at the beginning, as people are waiting to see how this will develop and at various points during the conference when interest may seem to be waning. Consider preparing a few colleagues to encourage discussion by having them ready to respond to the moderator’s postings, ask questions or post their own ideas at times when the action needs to get started or participation is slow.
• Evaluation: Have a routine “post mortem” after each conference where participants, by way of an evaluation, can suggest what learnings they may glean and what could have been done to make the conference more helpful, specifically for them.
• Technical: Electronic conferences should be held in a venue separate from the one people use for normal discussions. This way, regular users are less likely to feel they are interfering with or interrupting the conference. Electronic conferencing can be enjoyable as well as efficient and convenient. Giving some thought to how the conference will progress before it even starts will help to make it a valuable and enjoyable experience for all.
Meetings are a way of life in every business. Meetings can be a source of tremendous frustration. Meetings are also costly: put six people in a weekly staff meeting, and you've eaten up $10,000 worth of time. Total quality management, business process re-engineering, team management, and other techniques of the 90's aren't helping---most of these techniques actually increase the number of meetings people attend. Because meetings are so expensive and so inefficient and so dissatisfying, it's no surprise that there are lots of software developers working on tools to improve meetings.
These tools span a wide range of meeting assistance and support tasks. At the low end, software schedulers keep track of people, appointments, and resources to coordinate meeting times and places. In the middle are tools which help groups by improving communications. This includes conferencing systems and bulletin board packages, which extend "meeting space" outside of the meeting room by letting participants discuss issues without having to sit together. Other mid-range tools are designed to assist communications during a meeting. Video and audio conferencing hardware can be integrated with personal computers to link people in diverse locations for a single meeting. Shared drawing and editing tools also help groups work on a single document or share a visual concept easily.
At the high end are systems with much loftier goals: the complete reinvention of the meeting process. Developers of these systems have developed ways of completely changing the way meetings are held, and they have numbers from customers proving massive and dramatic improvements in productivity. But these benefits come at a cost---attendees must stop thinking of meetings as a waste of time and start thinking of meetings as an opportunity to make decisions and share information.
The low end of the meeting support market focuses mainly on scheduling meetings and managing calendars. Although there are many products available for standalone use or which support only a single platform, only a few vendors have taken an enterprise-wide approach to scheduling. Even so, any organization with truly disparate platforms will find it impossible to find a vendor willing to support all popular platforms for this relatively simple task.
In evaluating group scheduling systems, network managers must keep in mind the underlying politics of scheduling. These are generally more important to the success of a group scheduler than quality of user interface or performance. If the group scheduler cannot successfully emulate people’s behavior regarding their own personal calendar, then it will not be accepted into the workplace. Groupware of this type must fit into the organization; it is not reasonable to expect people to change the way they operate simply to accommodate an appointment-scheduling program.
Traditional meetings are same-time, same-place activities everyone has to be in the same room at the same time. Software and hardware, which extends the meeting room across both time and space, can substitute for some face-to-face meetings, empower people in remote locations, and improve face-to-face, meetings by making everyone better prepared.
The oldest alternative to face-to-face meetings is computer conferencing systems (sometimes called bulletin boards, although purists make a distinction between the two). These conferencing systems grew out of multi-user systems and often: support both microcomputer and dumb terminal interfaces.
Most conferencing systems do little more than let people exchange information and follow a single message and its associated discussion. The largest multi-platform conferencing system of this type is the Usenet News system. With literally dozens of public-domain and commercial "news readers," and a good selection of minicomputer-based servers, a simple conferencing system can truly encompass all corporate computing platforms, including dumb terminals, all microcomputer systems, on up to window system terminals. Other commercial products which support multiple platforms include Digital's (800/DIGITAL) DEC Notes, Lotus' (800/522-6752) Notes, and Pacer Software's (800/722-3702) PacerForum.
Making Meetings Better
Let me explain how to make the meetings better with a product called GroupSystems. It isn’t a single package. It's actually a suite of software tools (sixteen in the DOS version, fewer in the Windows version) which automate and enhance many of the processes which occur in meetings. A meeting using GroupSystems requires a personal computer for each participant and a "facilitator," someone to lead the meeting and choose which GroupSystems tool is most appropriate to the task at hand.
For example, suppose you want to have a meeting to help decide on a new name for your company. In the GroupSystems world, the meeting would look like this. First, participants in the meeting would brainstorm ideas using the Electronic Brainstorming tool. Each participant would enter as many ideas as they could think of during a defined time period, say 10 minutes. As ideas were typed in, GroupSystems would shuffle them around and send them to other participants. By seeing the ideas of others, presumably, you come up with your own possibilities.
GroupSystems advocates claim two advantages over manual meetings: participants can type in more ideas more quickly than anyone could possibly write them down because everyone is typing at the same time. Each idea is evaluated on its own merits, rather than based on who said it. Because tools like Electronic Brainstorming are anonymous, people who are normally afraid to bring up opinions in a meeting will be able to bring their best ideas without fear. ? In most professional meetings, this anonymity is rarely abused.
Changing the Face
Group Systems does not augment existing meetings. When a company buys into, they are buying much more than a software package. To properly use the system, facilitators must be trained in maximizing meeting productivity using these tools---because GroupSystems changes the way companies hold meetings. Bringing in GroupSystems is not a trivial investment. GroupSystems requires a PC in front of each user, Windows or DOS, a LAN (any popular microcomputer LAN package will work) to link them together, and a facilitator's station to control the meeting tools. GroupSystems also uses a shared screen at the front of the room which has to be large enough for everyone to see. With a base software and training cost of $25,000, building a meeting room for GroupSystems usually costs about $100,000.
Electronic Discussions
We've all heard so much hype about the potential of computer mediated communication to revolutionize teaching that we've begun to dismiss it automatically. We need to recognize, though, that it's not all hype. Even once you've discounted the snake oil salesmen selling off-the-shelf electronic course guides, style checkers and "interactive" computer-assisted learning programs, in fact there are still some startling opportunities. There are many reasons to expect that computer-mediated written discussions -- to pick the one that I'm most interested in -- should afford unprecedented learning opportunities, combining the flexibility and interactive engagement of oral conversation and the power of written language to foster reflection and allow complex ideas to be accumulated, revised, extended and polished.
But there haven't been many demonstrations of this potential. Indeed, the most common consequence of setting up an "electronic discussion group" for a university class or a group of faculty at an institution, or a set of colleagues with common interests, is a flurry of initial greetings ("Hello, everyone, isn't it great to have this new way to communicate"), followed by an enduring silence. The flurry may last somewhat longer for students in class-oriented discussions -- especially if participation is made a course requirement -- but even in those cases, most often the quality of the participation quickly becomes perfunctory and unengaged . . . usually not long before the instructor quietly allows the requirement to lapse.
To think about why this happens, and what we might do to avoid it, it's important to be clear about what sorts of programs and situations we're talking about. For many people, "it's all e-mail," but that oversimplification masks some distinctions that are worth making.
There are a number of ways we can group such programs to help us think about the characteristics of the different kinds of thing we're talking about here. One is to distinguish between "synchronic" and "asynchronic" types. Synchronic programs work in "real time"; that is, you write, someone reads immediately, and the text is gone, usually scrolling up the screen to oblivion. These include structures ranging from Internet or local "chat rooms" to highly developed sites, where conversations take place in virtual environments which can be fairly richly detailed. On the other hand, "asynchronous" programs like list servers and bulletin boards tend more toward the status of written correspondence -- or even publication. Messages persist (for instance, in your incoming mail) until they're read, and in fact can be easily saved after reading, and responded to at your convenience. Most programs used in classes other than computer-dedicated writing classes are of this latter kind.
Electronic messaging is more than just text messages passed between human writers and readers -- it offers a great potential in our environment to automate a great deal of routine data passing as well. These notes are devoted to exploring the topic to illustrate some of this potential and to helping you make some wise investments upon which you can grow a flexible, robust capability. Don't let the growing pains and a seemingly endless supply of warts divert your attention too much.
The first broadening of use of e-mail for more than the accustomed interpersonal communications is command communications. It is the best replacement for the traditional telegram-style record message. This is the market that the Defense Message System is targeting.
The second use is in automated systems where at least one end -- either the originator or the recipient -- is a machine rather than a human. Secure, multipurpose e-mail is an extremely good idea -- and one whose time came some years ago. Unfortunately, the impediments to a deployed, usable system have been considerable, and the worst ones largely unforeseen.
On the other hand, this litany of growth pains should really be put into the perspective that e-mail is a very powerful tool ... that has improved enormously in a fairly short period of time. E-mail should be the choice of first resort for the enveloping definition for almost any information system. Including 'tactical' ones. If it fits, look no farther.
Electronic Publishing
Traditional publishing involves four steps. First the authors produce their material for review by editors working on behalf of publishers. Material found suitable for a publisher is then sent to be typeset, to format the content into individual pages with a chosen style. These pages are then reproduced in multiple sets by putting ink on paper, and are bound into individual books and journal issues. Finally these are distributed to the audience by post to mailing lists of subscribers, book club members, libraries with standing orders and people who order books on line, or through retail outlets like bookstores and news agents.
Computers have played certain parts in this process for some time. Authors use word processors to build up, revise and print the source material, and more complex typesetting software is used to format pages with humans putting in the required commands to specify type fonts and sizes; pages sizes and partitions; insertion of figures, equations and footnotes; linking parts from different sources, such as chapters by multiple authors or reproduction of existing material, into a complete volume etc.
Most of you would be familiar with MS Word, and some of you may have used Latex, which formats an ASCII text file with embedded type- setting commands, into a DVI file specifying the content of each page, and this is further processed using a DVI to printing file (such as PDF or Postscript) converter which specifies in minute detail what kind of symbol to put onto each page where. Desktop publishing software basically combines word processing with easy to use typesetting software so that an author or editor can produce camera ready pages to be sent to a printer on his own PC, while HTML is a desktop publishing language that specifies the content and format of single pages for output on a computer screen with provision to add colour, sound, video, etc. The old equipment that were used to do the job, typewriters, molten lead typesetting machines, even paper typesetting machines (to produce masters for offset printers) are hardly used these days.
While computers have also played some part in controlling printing machines and in helping with the mailing and selling of printed material, their impact there has been much less fundamental, since they have not changed the basic process of putting ink on paper and distributing the paper piles. This is a highly inefficient process since the paper contributes almost all the weight, but the information is only carried by the ink. It takes organization to record, store and move around all that heavy bulk. In fact, one reason authors have to go through publishers to publish is the latter control the physical distribution system: while authors can produce content and make copies on their own, they lack means to put the copies into the libraries and retail shops, or to use large mailing lists to send copies to readers.
The Internet has radically changed this: Content is now specified as modulations of electromagnetic waves, conducted instantaneously across the world via wires, satellite links and optical fibres, instead of ink on paper moved around on lorries and aeroplanes. With numerous search engines crawling the web looking at every page and cateloging the content, it does not take long before your pages would turn up in a search list of someone looking for related material.
In short, with the help of PC on Internet, anyone can write, format and distribute his writings in the most direct way. However, while this solves one problem, it creates a new sets of issues for authors and publishers: Content represented in this way is also easily reproduced, without any graphical quality loss nor the work of copying, collating and binding. The previous exclusivity of control is now lost. For commercial publishing, the question is how to get paid when someone reads something you own. For scholarly publishing, the issue is establishing who published a particular piece of work at what time.
Information Systems Security and Control
There is a little doubt that business use of computers is increasing – to the point where e-commerce business require all of the components to be functioning 24 hours a day.. in this environment managers need to know what threats they face and what technologies exist to protect the system. there are three aspects that affect all businesses but are particularly important in e-commerce: 1. interception of transmissions, 2. attacks on servers, and 3. monitoring systems to identify attacks.
Many potential threats exist to information systems and the data they hold. The complicated aspect is that the biggest information threat is from the legitimaste users and developers. Purely by accident, a user might enter incorrect data or delete important information. A designer must understand an important function and the system will provide erroneous results. An innocent programming mistake could result in incorrect or destroyed data. Minor changes to a frail system could result in a cascading failure of the entire system.
We can detect and prevent some of these problems through careful design, testing, training and backup provisions. However, modern information systems are extremely complex. We cannot guarantee they will work correctly all of the time. Plus, the world poses physical threats that cannot be avoided: hurricanes, earthquakes, floods and so on. Often, the best we can do is build contingency plans that enable the company to recover as fast as possible. The most important aspect of any disaster plan is to maintain adequate backup compiles. With careful planning, organisation, and enough money, firms are able to provide virtually continuous information systems support.
33.2 System Vulnerability and Abuse
As our society and the world itself come to depend on computers and information systems more and more, systems must become more reliable. The systems must also be more secure when processing transactions and maintaining data. These two issues, which we address in this lesson the biggest issues facing those wanting to do business on or expand their operations to the Internet. The threats are real, but so are the solutions.
Threats to Computerised Information Systems
• Hardware failure
• Fire
• Software failure
• Electrical problem
• Personnel actions
• User errors
• Terminal access penetration
• Program changes
• Theft of data, services, equipment
• Telecommunications problems
System Quality Problems: Software and Data
It would be nice to have a perfect world, but we donÕt. Defects in software and data are real. You as an end user can't do much about the software, but you can do something about the data you input.
Bugs and Defects
The term bug, used to describe a defect in a software program, has been around since the 1940s and 1950s. Back then, computers were powered by vacuum tubes - hundreds and thousands of them. Grace Hopper, an early pioneer, was troubleshooting a computer that had quit running. When her team opened the back of the computer to see what was wrong, they found a moth had landed on one of the tubes and burned it out. So the term "bug" came to describe problems with computers and software.
With millions of lines of code, it's impossible to have a completely error-free program. Most software manufacturers know their products contain bugs when they release them to the marketplace. They provide free updates and fixes on their Web sites. That's why its a good idea not to buy the original version of a new software program but to wait until some of the major bugs have been found by others and fixed by the company.
Because bugs are so easy to create, most unintentionally, you can reduce the number of them in your programs by using the tools discussed in other chapters to design good programs from the beginning. Many bugs originate in poorly defined and designed programs and just keep infiltrating all parts of the program.
The Maintenance Nightmare
You simply can't build a system and then ignore it. It needs constant and continual attention. The fact is that half of a company's technology staff time is devoted to maintenance.
When you're considering organizational changes, no matter how minor they may seem, you must consider what changes need to be made to the systems that support the business unit. Keep in mind that software is very complex nowadays. You just might have to search through thousands or millions of lines of code to find one small error that can cause major disruptions to the smooth functioning of the system.
In the SDLC lesson, we stress good system analysis and design. How well you did back then will play out in the maintenance of the system. If you did a good job, maintenance will be reduced. If you did a poor job analyzing and designing the system, maintenance will be a far more difficult task.
Data Quality Problems
Let's bring the problem of poor data quality closer to home. What if the person updating your college records fails to record your grade correctly for this course and gives you a D instead of a B or an A? What if your completion of this course isn't even recorded? Think of the time and difficulty you'll experience getting the data corrected.
Information Systems security is everyone's business. Use antivirus software on your computer and update it every 30-60 days. The "it won't happen to me" attitude is trouble. Many system quality problems can be solved by instituting measures to decrease the bugs and defects in software and data entry.
Creating a Control Environment
How do you help prevent some of the problems we've discussed? One of the best ways is to introduce controls into your Information System the same as you might in any other system: through methods, policies, and procedures.
Think about what a typical company does when it builds a new office building. From the beginning of the design phase until the building is occupied, the company decides how the physical security of the building and its occupants will be handled. It builds locks into the doors, maybe even designs a single entry control point. It builds a special wing for the executive offices that has extra-thick bulletproof glass. Fences around the perimeter of the building control the loading docks.
These are just a few examples to get you to think about the fact that the company designs the security into the building from the beginning. You should do the same thing with an Information System. It's no different from any system that requires preplanning and well-thought-out policies and procedures before the building begins.
Let's look at the two distinct types of controls: general controls, which focus on the design, security and use of computer programs and data files, and application controls, which are concerned with the actual application programs.
General Controls
General Controls in Information Systems consist of the systems software and manual procedures used to control the design, security, and use of the programs and the data files in the overall system. General controls would be the overall security system, which may consist of outside door locks, fencing around the building, and employee passes. General controls wouldn't be concerned with what happens in one particular area of the building.
• Implementation Controls: When you use implementation control methods, you audit the development procedures and processes to make sure they conform to the business's standards and policies. Were all the steps completed, or did you skip some of them? What input did users and management have in the design and implementation of the system? Were managers allowed to sign off on milestones during the development process, or were they left out of the loop altogether? There is a reason why you have to use good, sound development procedures.
• Software and Hardware Controls: How is your system software installed, maintained, and used? What security measures are in place to ensure only authorized users are allowed access to your system? Are you using the latest version of virus protection software? These concerns are part of the software controls you should develop.
Companies control all of their manufacturing equipment, office supplies, and production tools--or at least try to. They should apply the same hardware controls to computer equipment as they would any other piece of equipment. Sometimes they don't. Laptop computers are especially vulnerable to theft and abuse: Companies seem to be very lax about employees borrowing laptops and then never returning them.
• Computer Operations and Data Security Controls: Computer operations controls are the responsibility of the Information Technology Department staff and are concerned with the storage and processing of data. Often overlooked in this area is the need for protecting the system documentation that details how jobs are processed, how data are stored, and how the systems operate. Someone who steals this information could do serious damage.
Whether you're working with current data or archived data, you still need to protect them from unauthorized access or use. The movie "The Net" depicted a fictionalized version of data theft and manipulation. While it may have been an exaggeration, this could happen if a company doesn't do enough to protect its data.
• Data security controls should consist of passwords that allow only certain people access to the system or to certain areas of the system. While you may want to grant employees access to their payroll data or 401K data through an Intranet, you must make sure they can access only their information and not that of any other employee. You wouldn't want a co-worker to be able to access your paycheck information, would you?
Application Controls
We've talked about controls for the general use of an Information System. Application controls are specific controls within each computer application used in the system. Each activity in the system needs controls to ensure the integrity of the data input, how it's processed, and how it's stored and used.
• Input Controls :Are the data accurate and complete? We used an example earlier of a course grade being entered incorrectly. If your system had a method to check the data on the input documents against the actual data entered into the system, this kind of error could be caught and corrected at the time it was entered. Many companies are using source data automation to help eliminate input errors.
• Processing Controls: As the name describes, processing controls are used during the actual processing of the data. If Suzy says she entered 100 items into the system on Tuesday, your application program would have a method of checking and reporting the actual number of data entries for that day. Not that you think Suzy is lying; you just need to have a method of verifying and reconciling data entered against data processed.
• Output Controls: Is the information created from the data accurate, complete, and properly distributed? Output controls can verify who gets the output, and if they're authorized to use it. You can also use output controls to match the number of transactions input, the number of transactions processed, and the number of transactions output.
Security and the Internet
We can't stress enough the importance of security for Intranets, Extranets, and the Internet. Organizations must control access through firewalls, transaction logs, access security, and output controls. Software programs that track "footprints" of people accessing the system can be a good way to detect intruders in the system, what they did, what files they accessed, and how they entered your system initially.
The most important point is that you get the software, use it, and protect one of your most important organizational resources.
Developing a Control Structure: Costs and Benefits
You should be realistic about security and system controls. If you set up five layers of entry into your Web site, people probably won't access it that much. They'll either ignore it or find a way around your controls. You have to analyze the system and determine those areas that should receive more security and controls and those that probably can use less.
Returning to our building analogy, the Executive Wing, which houses the CEO and other key executives, will probably have more locks on the doors, more entry barriers, than the area the data workers occupy. You can't check absolutely every person who traverses the hallways each day, but you can have regular employees wear badges that readily identify them.
The Role of Auditing in the Control Process
Companies audit their financial data using outside firms to make sure there aren't any discrepancies in their accounting processes. Perhaps they audit their supply systems on a periodic basis to make sure everything is on the up-and-up. They should also audit their Information Systems. After all, information is as important a resource as any other in the organization. MIS audits verify that the system was developed according to specifications, that the input, processing, and output systems are operating according to requirements, and that the data are protected against theft, abuse, and misuse. In essence, an MIS audit checks all the controls we've discussed in this lesson.
We mentioned earlier that a bank teller wouldn't be the one to count the money in the till at the end of the workday. To ensure validity in an MIS audit, you would use someone totally disconnected from the system itself. Usually companies hire outside auditors to verify the integrity of the system, since they won't have any vested interest in hiding any flaws.
Ensuring System Quality
There's a reason why we explained all those methods and procedures and processes in previous chapters for building good, solid Information Systems. They ensure system quality so that the product produced by the system is as good as it can be.
Software Quality Assurance
Just as you must assure quality of other products and other work, you must assure the quality of your software.
Methodologies
It's easier to find the flaws in a system if you create all new systems and programs the same way every time. If you want to check the system, fix the system, add to the system, or audit the system, you won't have to spend time figuring out how it was built in the first place. In this case, predictability leads to efficiency. The documentation that most people fail to develop makes it easier to determine how the system is built and how it operates.
Most companies and most people spend the majority of their time in the programming phase of system development. Not a good idea. Just accept the fact that the more time you spend analyzing and designing a system, the easier the programming and the better the system. You will save a lot of time and headaches and money. Honest, it really does work that way!
Software Metrics
Be objective when you're assessing the system by using software metrics to measure your system. Emotions tend to cost money and use unnecessary resources. The text gives several good examples of metrics you can use to measure your system inputs, processes, and outputs. For metrics to be successful, they must be:
• Carefully designed
• Formal
• Objective
• Measure significant aspects of the system
• Used consistently
• Agreed to by users advance
Testing
You can't ignore testing as a vital part of any system. Even though your system may appear to be working normally, you should still verify that it is working according to the specifications. Walkthroughs are an excellent way to review system specifications and make sure they are correct. Walkthroughs are usually conducted before programming begins, although they can be done periodically throughout all phases of system development.
Once a system has been coded, it is much harder and more expensive to change it. We're beginning to sound like a broken record, but it's important that you understand and remember that the more work you do before the programming phase begins, the less trouble you'll have later. You can't just start pounding the keyboard and hope everything works out okay.
Quality Tools
Just as you would manage any big project--a house, a highway, a skyscraper--you must manage the entire systems development project. You can do it much easier using project management software that allows you to keep track of the thousands of details, deadlines, tasks, and people involved in the project. This type of software also helps you keep everything in sync.
Data Quality Audits
We spoke earlier of MIS audits, which check the system and its general controls and application controls. Data quality audits verify the data themselves. Many of the principles we discussed in the MIS audit apply to this type of audit. A company should formally record the number and types of errors customers report. Using this record can help managers do data quality audits by giving them ideas of where they can start looking for problems or areas that need to be improved.
A few comments regarding the three items in the text:
• Survey end users for their perceptions of data quality: How do they see it? Looking at your data through a different set of eyes can reveal problems you weren't aware of.
• Survey entire data files: This can be expensive and time-consuming, but very fruitful.
• Survey samples from data files: Make sure the sample is big enough and random enough to uncover problems.
Conclusion
Management information system will only reap the benefits if the companies gain insight to better align strategies and identify critical relationships and gaps along four key company dimensions – people, process, culture and infrastructure. information system provides a framework for companies to evaluate themselves relative to these dimensions. By understanding and improving alignment with these critical dimensions, companies can maximize the value and impact of information as a strategic corporate asset to gain competitive advantage.
Control the creation and growth of records despite decades of using various non-paper storage media, the amount of paper in our offices continues to escalate. An effective records information system addresses both creation control (limits the generation of records or copies not required to operate the business) and records retention (a system for destroying useless records or retiring inactive records), thus stabilizing the growth of records in all formats. reduce operating costs Recordkeeping requires administrative dollars for filing equipment, space in offices, and staffing to maintain an organized filing system (or to search for lost records when there is no organized system).It costs considerably less per linear foot of records to store inactive records in a Data Records Centre versus in the office and there is an opportunity to effect some cost savings in space and equipment, and an opportunity to utilize staff more productively - just by implementing a records management program.
Improve efficiency and productivity Time spent searching for missing or misfiled records is non-productive. A good records management program (e.g. a document system) can help any organization upgrade its recordkeeping systems so that information retrieval is enhanced, with corresponding improvements in office efficiency and productivity. A well designed and operated filing system with an effective index can facilitate retrieval and deliver information to users as quickly as they need it. Moreover, a well managed information system acting as a corporate asset enables organizations to objectively evaluate their use of information and accurately lay out a roadmap for improvements that optimize business returns. Assimilate new records management technologies A good records management program provides an organization with the capability to assimilate new technologies and take advantage of their many benefits. Investments in new computer systems whether this is financial, business or otherwise, don't solve filing problems unless current manual recordkeeping or bookkeeping systems are analyzed (and occasionally, overhauled) before automation is applied.
Ensure regulatory compliance In terms of recordkeeping requirements, China is a heavily regulated country. These laws can create major compliance problems for businesses and government agencies since they can be difficult to locate, interpret and apply. The only way an organization can be reasonably sure that it is in full compliance with laws and regulations is by operating a good management information system which takes responsibility for regulatory compliance, while working closely with the local authorities. Failure to comply with laws and regulations could result in severe fines, penalties or other legal consequences.
Minimize litigation risks business organizations implement management information systems and programs in order to reduce the risks associated with litigation and potential penalties. This can be equally true in Government agencies. For example, a consistently applied records management program can reduce the liabilities associated with document disposal by providing for their systematic, routine disposal in the normal course of business.
Safeguard vital information every organization, public or private, needs a comprehensive program for protecting its vital records and information from catastrophe or disaster, because every organization is vulnerable to loss. Operated as part of a good management information system, vital records programs preserve the integrity and confidentiality of the most important records and safeguard the vital information assets according to a "Plan" to protect the records. This is especially the case for financial information whereby ERP (Enterprise Resource Planning) systems are being deployed in large companies.
Support better management decision making In today's business environment, the manager that has the relevant data first often wins, either by making the decision ahead of the competition, or by making a better, more informed decision. A good management information system can help ensure that managers and executives have the information they need when they need it. By implementing an enterprise-wide file organization, including indexing and retrieval capability, managers can obtain and assemble pertinent information quickly for current decisions and future business planning purposes. Likewise, implementing a good ERP system to take account of all the business’ processes both financial and operational will give an organization more advantages than one who was operating a manual based system. Preserve the corporate memory an organization's files, records and financial data contain its institutional memory, an irreplaceable asset that is often overlooked. Every business day, you create the records, which could become background data for future management decisions and planning. foster professionalism in running the business A business office with files, documents and financial data askew, stacked on top of file cabinets and in boxes everywhere, creates a poor working environment. The perceptions of customers and the public, and "image" and "morale" of the staff, though hard to quantify in cost-benefit terms, may be among the best reasons to establish a good management information system.
Reference
Managing Information Systems: An Organisational Perspective (2nd Edition). Prentice Hall, 2004
Management Information Systems: Managing the Digital Firm (8th Edition). Prentice Hall, 2004
Information Technology for Management : Transforming Organizations in the Digital Economy (4th edition). Wiley, 2004
Post, Gerald V. and David L. Anderson. Management Information Systems:
solving business problems with information technology. McGraw-Hill Higher
Education, 2003