- RESEARCHDistance Learning at AIU is enhanced by vast academic resources and innovative technologies build into the Virtual Campus: Hundreds of self-paced courses with video lectures and step by step lessons, thousands of optional assignments, 140,000 e-books, the Social Media & Networking platform allowing collaboration/chat/communications between students, and MYAIU develop students holistically in 11 areas beyond just academics.
- PROGRAMS OFFERED
- Areas of Study
- Courses and Curriculum
- Open Courses
- Register for a Program
- Associate Program
- Associate in Addiction Counseling
- Associate in Agriculture Food And Resources
- Associate in Anti Terrorism Security
- Associate in Behavior Analysis In Special Education
- Associate in Bioethics
- Associate in Climatology
- Associate in Cultural Theological Communication
- Associate in Culinary Arts
- Associate in Ecotechnology
- View all Associates Programs
- Bachelor Program
- Bachelors in Community Development
- Bachelors in Environmental Science
- Bachelor in Education (B.Ed, BS)
- Bachelors in Economics
- Bachelors in Entrepreneurship
- Bachelors in Financial Administration
- Bachelors in Human Resource Management
- Bachelors in Linguistics
- Bachelors in Nutritional Science
- Bachelors in Occupational Health and Safety
- Bachelors in Psychology
- View all Bachelor Programs
- Doctorate Program
- Doctor | of Biology (PhD)
- Doctorate in Business Administration (DBA, PhD)
- Doctor of Economics (PhD)
- Doctor of Electrical Engineering (D.Sc, PhD)
- Doctor of Finance (PhD)
- Doctorate in International Relations
- Doctorate in Information Technology (D.Sc)
- Doctor of Legal Studies (PhD)
- Doctor of Project Management (PhD)
- Doctor of Sociology (PhD, D.Sc)
- Doctorate in Sustainable Natural Resources Management
- View all Doctorate Programs
- Master Program
- Postdoctoral Program
- Postdoctoral in Animal Science
- Postdoctoral in Anti Terrorism Security
- Postdoctoral in Behavior Analysis In Special Education
- Postdoctoral in Bioethics
- Postdoctoral in Blockchain Technology and Digital Currency
- Postdoctoral in Business Management
- Postdoctoral in Cloud Computing
- Postdoctoral in Computer Engineering
- View all Postdoctoral Programs
AIU offers a wide range of majors in areas including the Arts, Business, Science, Technology, Social, and Human studies. More than 120 degrees and programs are available for adult learners at the associate’s, bachelor’s, master’s, doctoral and postdoctoral level. - VIRTUAL CAMPUS
Distance Learning at AIU is enhanced by vast academic resources and innovative technologies build into the Virtual Campus: Hundreds of self-paced courses with video lectures and step by step lessons, thousands of optional assignments, 140,000 e-books, the Social Media & Networking platform allowing collaboration/chat/communications between students, and MYAIU develop students holistically in 11 areas beyond just academics.
- ALUMNI
The world is YOUR campus!”, that is the message of AIU’s month magazine Campus Mundi. Hear the voices and see the faces that make up AIU. Campus Mundi brings the world of AIU to you every months with inspirational stories, news and achievements by AIU members from around the world (students and staff are located in over 200 countries).
Cybersecurity Trends: Protecting Data in the Digital Age

Want to know what is Zero Trust Architecture?
Find out some of the best practices for cloud security.
How can AI help in cybersecurity?
Use your research skills and write about how are the emerging technologies like quantum computing expected to impact the future of cybersecurity, and what steps are being taken to address potential vulnerabilities associated with quantum advancements? Use credible sources such as academic journals, educational websites, and expert interviews to gather information and present a well-rounded answer.
(Login to your student section to access the AIU Additional Resources Library.)
Cybersecurity Trends: Protecting Data in the Digital Age
In an era where digital transformation drives business innovation and reshapes industries, cybersecurity has become more critical than ever. As organizations increasingly rely on digital tools and platforms, the threat landscape has evolved, bringing new challenges to data protection. From sophisticated ransomware attacks to emerging technologies like artificial intelligence (AI) in cyber defense, understanding the latest cybersecurity trends is essential for safeguarding sensitive information in the digital age.

Source: Paloalto
Ransomware: The Relentless Threat
Ransomware attacks have surged in recent years, becoming one of the most pervasive threats in cybersecurity. These attacks involve malicious software that encrypts a victim’s data, with attackers demanding a ransom for the decryption key. High-profile cases, such as the Colonial Pipeline attack, highlight ransomware’s devastating impact on critical infrastructure and businesses.
To combat ransomware, organizations invest in advanced threat detection systems, regular data backups, and comprehensive incident response plans. Cyber insurance is also becoming crucial to risk management strategies, offering financial protection against potential losses.
Zero Trust Architecture: Trust No One
The traditional perimeter-based security model, where everything inside the network is trusted, could be more effective in today’s digital environment. Enter Zero Trust Architecture (ZTA), a framework that assumes no entity, whether inside or outside the network, should be automatically trusted.
ZTA requires continuous verification of user identities and strict access controls based on the principle of least privilege. This approach significantly reduces the risk of unauthorized access and lateral movement within networks, making it a cornerstone of modern cybersecurity strategies.
AI and Machine Learning in Cyber Defense
Artificial intelligence (AI) and machine learning (ML) revolutionize cybersecurity by enabling faster and more accurate threat detection. These technologies can analyze vast amounts of data in real-time, identifying patterns and anomalies that may indicate a cyber threat.
AI-driven cybersecurity tools are enhancing the capabilities of security operations centers (SOCs), allowing for proactive threat hunting and automated incident response. However, as cybercriminals also begin leveraging AI, the race between attackers and defenders intensifies.
Cloud Security: Safeguarding the Digital Frontier
As businesses migrate to cloud environments, the security of cloud-based data and applications has become paramount. While cloud providers implement robust security measures, the shared responsibility model means organizations must also actively secure their data.
The adoption of cloud security posture management (CSPM) solutions is on the rise. These solutions help organizations identify and mitigate configuration vulnerabilities. Encryption, multi-factor authentication (MFA), and continuous monitoring are essential for protecting data in the cloud.
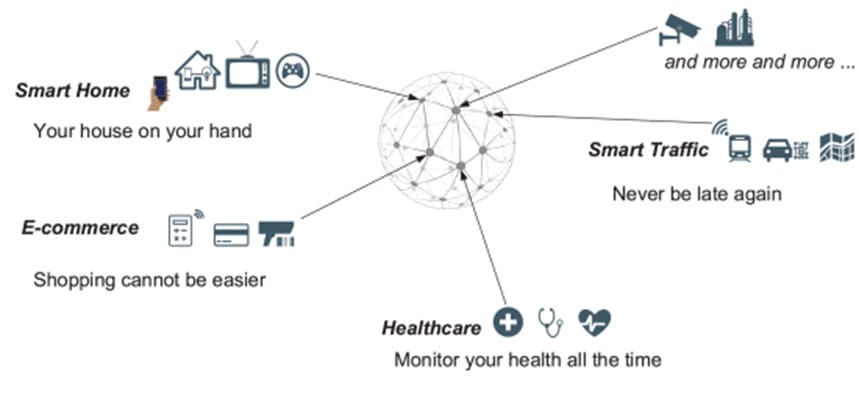
IoT applications
Source: Ieeexplore
IoT Security: The Expanding Attack Surface
The Internet of Things (IoT) transforms industries by connecting devices and systems for greater efficiency. However, each connected device represents a potential entry point for cyberattacks, expanding the attack surface significantly.
Ensuring the security of IoT devices requires a multi-layered approach, including device authentication, secure firmware updates, and network segmentation. As IoT continues to increase, developing industry-wide standards for IoT security is becoming increasingly urgent.
Data Privacy and Compliance: Navigating Regulatory Challenges
According to secondary research, with the rise of data breaches and the growing importance of data privacy, regulatory frameworks like the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) have been implemented to protect consumers’ personal information.
Compliance with data privacy regulations is not just a legal requirement but a critical component of building customer trust. Organizations invest in data governance frameworks and privacy-enhancing technologies (PETs) to ensure compliance and protect sensitive data.
Human Factor: The Weakest Link
Despite technological advancements, human error remains one of the leading causes of data breaches. Phishing attacks, in particular, continue to exploit human vulnerabilities, tricking employees into revealing sensitive information or clicking on malicious links.
Enhancing cybersecurity awareness through regular training and simulations is essential for reducing the risk of human error. Organizations are also adopting behavioral analytics to detect unusual user activity that may indicate a compromised account.
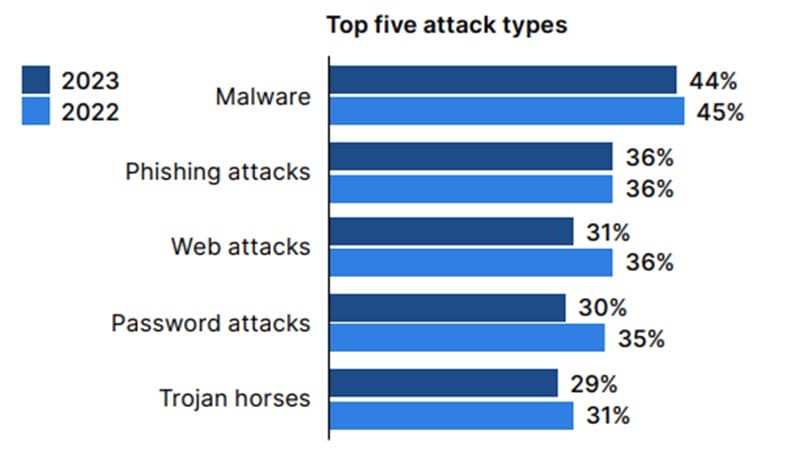
Common attacks in 2023
Source: Fortinet
Cybersecurity Skills Gap: Bridging the Divide
The demand for cybersecurity professionals is outpacing supply, creating a significant skills gap. This shortage poses a challenge for organizations seeking to build robust security teams capable of defending against increasingly sophisticated threats.
To address the skills gap, companies are investing in cybersecurity training programs, partnering with educational institutions, and leveraging managed security service providers (MSSPs). Additionally, automation and AI augment human capabilities and ease the burden on security teams.
Adapting to the Evolving Threat Landscape
In the digital age, cybersecurity is not a static field; it constantly evolves in response to new threats and technological advancements. Organizations must remain vigilant, stay informed about the latest trends, and adopt a proactive approach to data protection. By investing in cutting-edge technologies, fostering a culture of security awareness, and continuously assessing and updating security strategies, businesses can effectively protect their data and maintain resilience against cyber threats.
As we move forward, collaboration between the public and private sectors and ongoing innovation in cybersecurity will be crucial in safeguarding the digital future.
If this article triggers any interest in cybersecurity trends, then AIU offers a list of Mini courses, Blogs, News articles and many more on related topics that one can access such as:
Quantum Computing on Cybersecurity – Atlantic International University (aiu.edu)
Cybersecurity in IoT and Smart Devices
AIU also offers a comprehensive array of recorded live classes spanning various subjects. If any topic piques your interest, you can explore related live classes. Furthermore, our expansive online library houses a wealth of knowledge, comprising thousands of e-books, thereby serving as a valuable supplementary resource.
AI and Freelancing by Jay Bachahally
AI with coding github copilot and chat gpt by Jay Vijayasimha
Using Nanoscience for environmental repair and preservation by Tyler Gleckler
JavaScript Programming Essentials by Jay Radhakrishnan
Cybersecurity Trends for 2023 & What to Expect
These tech trends will dominate in 2023: Cybersecurity, layoffs on horizon this year
References
Colonial Pipeline hack explained: Everything you need to know (techtarget.com)
Behind the rise of ransomware – Atlantic Council
What is Zero Trust Architecture? | SANS Institute
How AI is Revolutionizing Cybersecurity: GenAI Threats and Solutions (eliassen.com)
How Artificial Intelligence is Transforming Cybersecurity | Infosec (infosecinstitute.com)
The Growing Role of Machine Learning in Cybersecurity – Palo Alto Networks
11 Cloud Security Best Practices & Tips in 2024 (esecurityplanet.com)
Securing the Internet of Things | ScienceDirect
2024-cybersecurity-skills-gap-report.pdf (fortinet.com)
Here’s how to address the global cybersecurity skills gap | World Economic Forum (weforum.org)
Reminder to our Dear Students,
Please ensure you are logged in as a student on the AIU platform and logged into the AIU Online
Library before accessing course links. This step is crucial for uninterrupted access to your learning
resources.
AIU Success Stories







Contact Us Today!
Begin Your Journey!
AIU’s Summer of Innovation and Growth gives you the ability to earn up to $5000 in tuition credit by completing free lessons and courses.
Whether you’re looking to acquire new skills, advance your career, or simply explore new interests, AIU is your gateway to a world of opportunities. With free access to 3400 lessons and hundreds of courses the ability to earn credits and earn certificates there’s no better time to start learning.
Join us today as a Guest Student and take the first step towards a brighter, more empowered future.
Explore. Learn. Achieve.

Contact Us
Atlantic International University
900 Fort Street Mall 905 Honolulu, HI 96813 [email protected]
Quick Links
Home | Online Courses | Available Courses | Virtual Campus | Career Center | Available Positions | Ask Career Coach | The Job Interview | Resume Writing | Accreditation | Areas of Study | Bachelor Degree Programs | Masters Degree Programs | Doctoral Degree Programs | Course & Curriculum | Human Rights | Online Library | Representations | Student Publication | Sponsors | General Information | Mission & Vision | School of Business and Economics | School of Science and Engineering | School of Social and Human Studies | Media Center | Admission Requirements | Apply Online | Tuition | Faculty & Staff | Distance Learning Overview | Student Testimonials | AIU Blogs | Register for Program | Privacy Policy | FAQ